Providers
In SleakOps a Provider represents the connection to your AWS Cloud, the credentials granted to SleakOps to it and the set of accounts created in order to properly manage the infrastructure.
On AWS, SleakOps will create an Organization with the name you selected and it will include a set of accounts into it.
In order to provide you with a clear view of your AWS cost and resources, SleakOps activates AWS Tags on your account. Specially SleakOps uses Cost Allocation Tags .
Let's create your provider on SleakOps
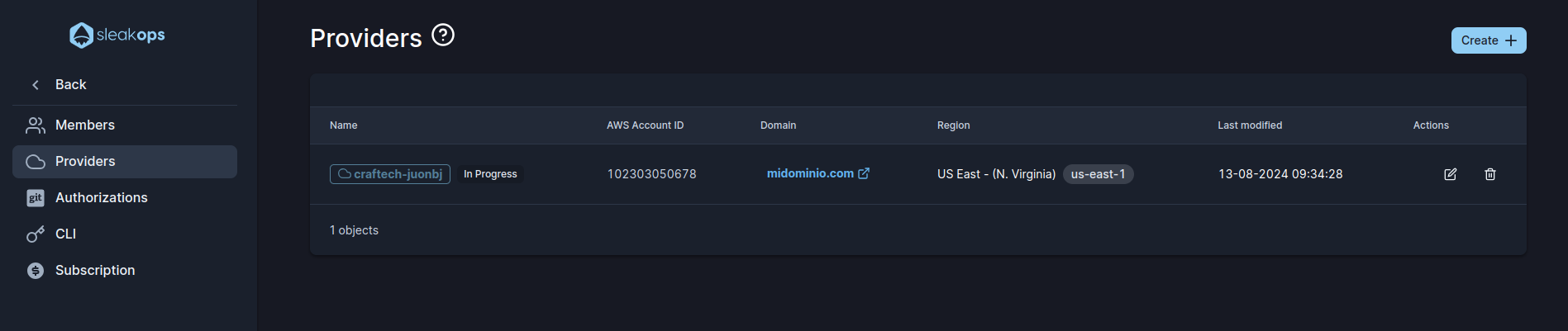
1. Navigate to the providers section
Into the Left Pane, access the Setting option and then Providers and then, at the top right corner, click on the Create button.
2. Set up basic Information
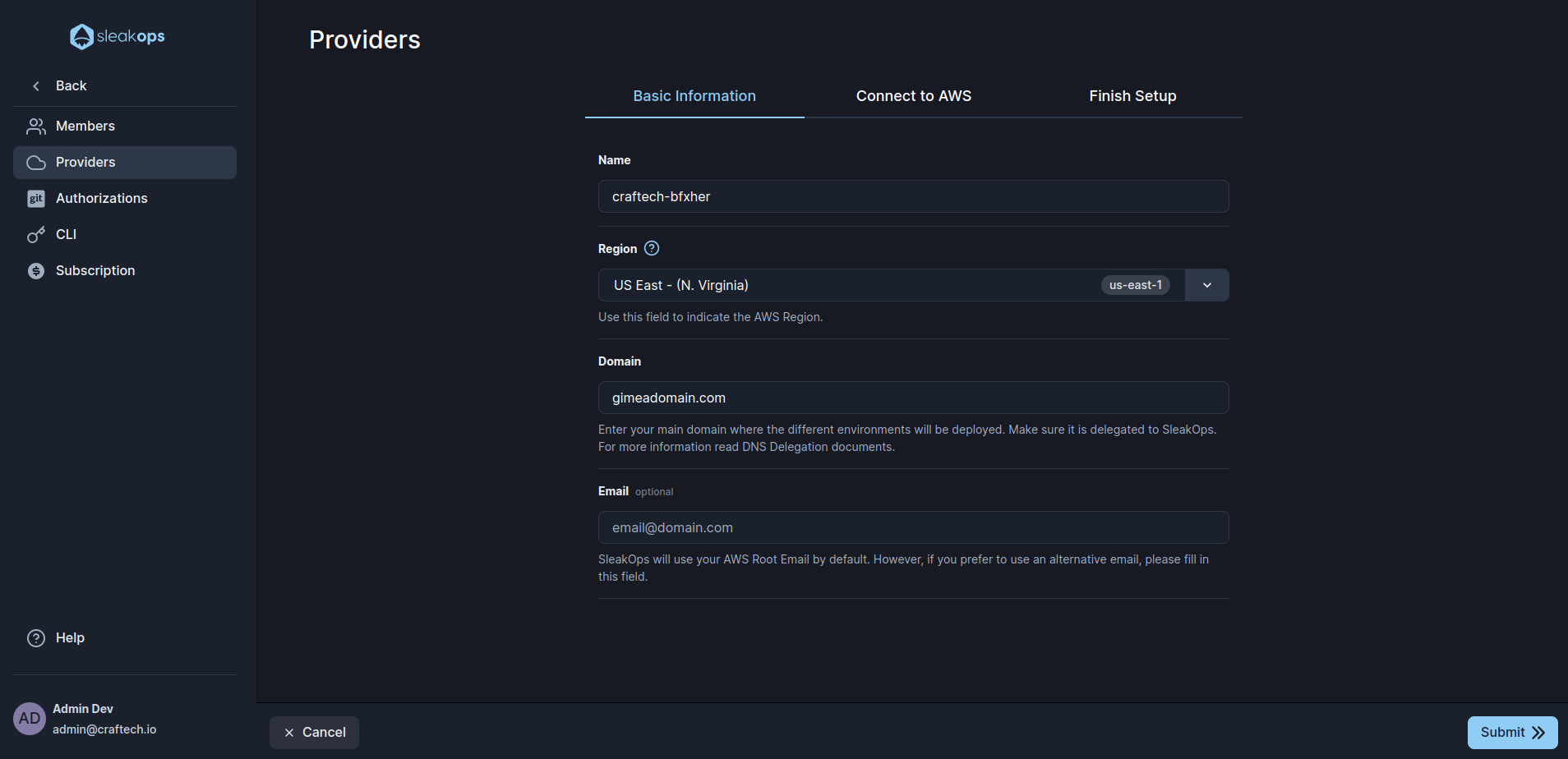
These are the settings you must define:
| Setting | Description |
|---|---|
| Name | Select a name for the Organizative Unit into AWS under the needed accounts will be created. |
| Region | AWS region to use. If you want to know more about them, you can visit this documentation https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/Concepts.RegionsAndAvailabilityZones.html. |
| Domain | Here you must provide the domain you own in which the different environments will be deployed. It must be delegated to the Primary Route53 of SleakOps manually. Follow the steps described on this https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/MigratingDNS.html. |
| By default SleakOps uses the email from the root account provided, If you want to use other email to register your SleakOps accounts in AWS, fill in this field. |
Once you've completed the form, click on Next to move forward.
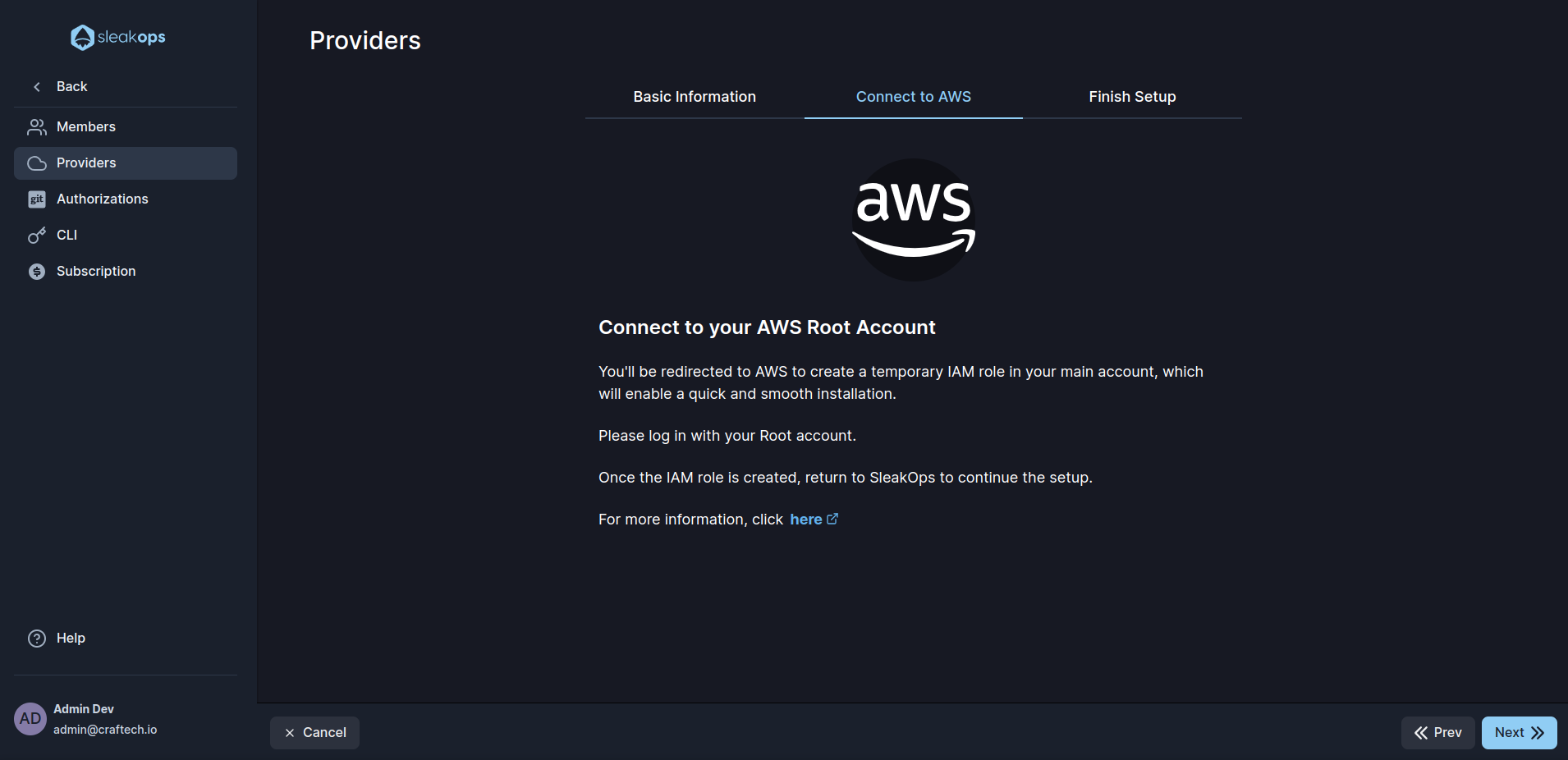
3. Connect to your AWS Root Account
You must be logged into your AWS Root Account.
To start installing your application, we need to connect to your AWS Root Account. Here's how to do it:
- By clicking the Next button, you’ll be redirected to AWS to create an IAM role in your main account called "SleakopsIntegrationRole".
- This role lets us access necessary resources, making installation quick and smooth.
- After installation, we will remove this role to keep your account secure.
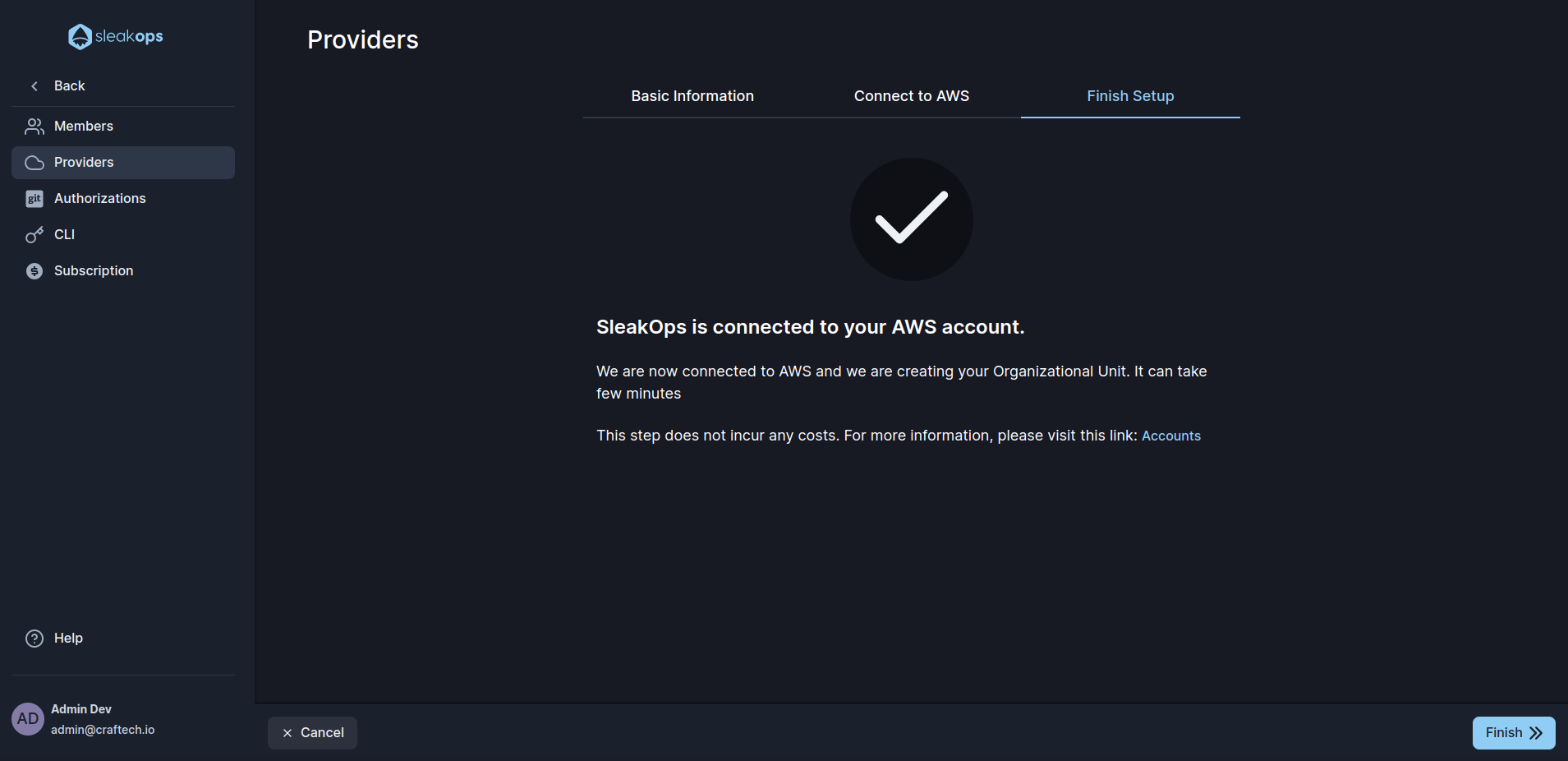
4. Ongoing Organizative Unit process started
Creating your Organizative Unit doesn't generate any cost on your AWS account 😃
Once the connection is established role is created, SleakOps will automatically start the Organizative Unit creation.
This process will take a few minutes.
5. Learn about the infrastructure architecture created by SleakOps for you.
In order to understand what was created on your AWS, please see Accounts.